I am happy to release the new RPMs of squid 3.5.12 for Centos 6 64bit, 32bit and CentOS 7 64bit.
The new release includes couple bug fixes and improvements.
I have also took the time to build the latest beta 4.0.3 RPM for CentOS 7.
The details about the the RPMs repository are at squid-wiki.
Why 3DES (triple DES)? or The fall of DES.
It is known in the cryptography world that since 1997 DES(IE single DES) is vulnerable to some attacks and there for is being considered to be unsafe for some uses. In order to resolve the DES issues the 3DES was implemented due to the ability to use the same fast cryptography machinery\chips that was used before and by that giving some time to the industry to find another more fit solution.
Some words about the DES encryption from Professor Gideon Samid:
Hashing compared to Encryption
The difference between hashing to encryption is the ability to recreate the original digested content. Hashes are meant to allow some kind of content validation verification based on the low probability of math collisions. To give a simple example about the subject we can use the Quadratic Formula:
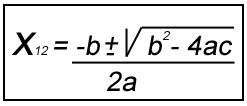
The formula defines that it is possible (or it is always the right answer) to have two answers to the same question\issue\variables.
Based on the fact\assumption that there is a possibility for two answers\solutions to the same unknowns+function we can use a function to describe more then one number. And in the case of computers which everything is some kind of a number we can convert the unknown numbers to octets.
Once there is no difference between numbers and\or octets and letters and we are in the function computation world. There we can use all sorts of functions\equations in order to describe all sorts of numbers and by that letters.
Eventually hashes are some kind of known functions which implements some way to reflect very big numbers or very big documents in some kind of output . Technically speaking it’s some function\method that is guaranteed to reflect very big numbers with probability(high or low) that multiple input values will be reflected with the same output number(128 bits for example).
In many levels of applications some hashes such as crc32\md5\sha-1\others are being used and these applications allow them-self to validate content integrity with a fully “vulnerable” hash due to the fact that the validated content do not exceed the function collision sizes.
I must admit that I have used MD5 and many other hashes for a very long time and the only collisions that I have seen that affected real world applications integrity are that of CRC32 hashes, maybe I have not seen enough yet!
And couple expert words from Professor Gideon Samid on hashing:
- Disclaimer: I am not a cryptography expert!
This RPMs release was tested for:
- ICAP 204\206 compatibility (non ssl)
- ECAP passthru adapter which digest response body using SHA256
- refresh_pattern variations
- StoreID patterns
- Basic load testing
- Basic ssl-bump usage in strict forward proxy mode
- Basic denial of memory leaks on a long period time of operation
- Basic build tests
All the above was done on a CentOS 7 x86_64 VMs.
I have not tested everything on CentOS 6 since it is assumed that if it works good on CentOS 7 there should not be a special reason for it to not work on CentOS 6.
More details about the repository at squid-wiki.
All The Bests,
Eliezer Croitoru
- I have been working on “Store ID – The hackers side of the feature“
- And I am planning an update to “Caching Dynamic Content using Adaptation” (which will not include ways to cache youtube)